With data surrounding us and networked into everything we do, the security of our data, both in transit and while at rest, is an obvious public safety issue. Which makes it puzzling why governments — whose principal job, since at least the time of Thomas Hobbes, is to keep us safe — have repeatedly sought to deliberately weaken the protocols that secure our data.
As with much else, the root of this seeming paradox can ultimately be traced to differences in threat paradigms: differences between what are considered to be the principal objects of security (meaning, that which is to be protected). Is it the state, or is it the people? Is it the network within a particular sovereign territorial space, or is it the undifferentiated global network as a whole? A new resource jointly published today by Citizen Lab and CIPPIC will hopefully help unpack these issues.
Generally speaking, government agencies navigate the world through a realist political lens (“realist” in the IR theory sense, à la Thomas Hobbes). From this perspective, the world is divided into territorially-based sovereign states who compete against each other for political advantage. One state’s gain is another’s loss. Through most of modern history, one part of this competition for power involved governments using various forms of cryptography to protect their communications and to hide their machinations from each other while simultaneously racing to find ways to crack each other’s secret codes. (An infamous version of this competition was popularized in the film, The Imitation Game, which told the story of Alan Turing and his Bletchley Park colleagues’ attempts to break Nazi Germany’s Enigma-machine cryptographic algorithms using some of the earliest computing machines.)
While these state-vs-state contests over code may have made sense when the world was neatly divided into territorially-segmented communication spaces, they no longer do. Government agencies that deliberately weaken cryptographic protocols to gain some momentary advantage over their opponents do so at the expense of their own citizens’ security. The reason that they do is that governments, companies, and citizens all over the world increasingly rely on the same communication technologies for everything they do.
National security concerns are not the only motivation for government agencies to weaken data security. Like intelligence agencies, law enforcement has also sought to keep cryptography contained or deliberately compromised, but for them the principal concern is about being able to investigate criminal behavior. It’s obviously much easier to solve a crime or chase down illegal activity if you can secretly listen in or watch what the criminals are doing. But as is the case as far as national security is concerned, a government agency can only gain such an advantage at the expense of the whole of society. Criminals and law-abiding citizens alike use the same communication systems: weaken them for one and you weaken them for all.
And yet continue to try to weaken them they do.
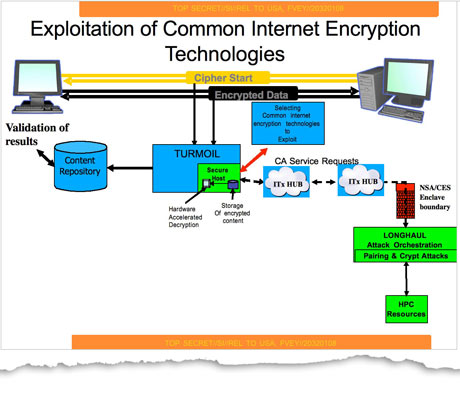
Time and again, government officials have used national security or lawful access justifications to argue for restrictions or special “back doors” on encryption. Time and again, computer scientists, engineers, and rights activists have argued the opposite case. Not always are the efforts to settle these debates undertaken in the open. One of the most serious revelations coming from the 2013 Edward Snowden disclosures showed that the NSA and its Five Eyes colleagues had surreptitiously foisted a deliberately weakened encryption standard (Dual EC ERGB) on the rest of the world, as part of a secret program codenamed “Bullrun.” Reports from the latest round of the International Organization of Standardization suggests they may still be up to such machinations.
There has been a lot written about these debates from all sides, but not much focusing in particular on the Canadian context. To be sure, it is not for lack of Canadian government agencies trying to influence the space. Canadian law enforcement and intelligence agencies have pushed for weakened encryption, back doors, company cooperation, or some kind of other “compromise” for lawful access as often as other governments do. Canada’s SIGINT agency, CSE, may have also had a hand in the NSA’s subterfuge around the weakened encryption protocol mentioned above. Meanwhile, for the Canadian public, the issue is only getting more salient. Many Canadians carry with them devices that feature full-disk, biometric-enabled encryption that only they can unlock. Can government agents compel them to do so when they are detained, arrested, or while crossing a border?
To help Canadians navigate these issues, today the Citizen Lab, in collaboration with CIPPIC, is releasing a report, entitled “Shining a Light on the Encryption Debate: A Canadian Field Guide,” authored by the Citizen Lab’s Lex Gill and Christopher Parsons and CIPPIC’s Tamir Israel. The report provides critical insight and analysis for policymakers, legal professionals, academics, journalists, and advocates who are trying to navigate the complex implications of encryption technology. It is designed to be a “field guide.” The report can be read top-to-bottom, but is also organized so that most sections can be reviewed as self contained references.
Now more than ever, encryption is vital to preserving and extending human rights. Encryption serves as an important guarantor of freedom of expression, opinion, privacy, anonymity, equality, and even physical safety for ordinary citizens, human rights activists, and journalists. With this latest report, we hope that those involved in encryption debates are better able to understand the full spectrum of issues related to the use and potential misuse of these technologies.